Auditing files on Windows Server

Recently some files went missing in very strict environment with all groups and rights made just right. Thing is, despite users, also third party program could modify files as well. Long story short - yes, it was that particular program that when changed some aspects in his own engine it didn't properly move files around share causing it to be deleted.
Of course, in those situations there is ping-pong between Administrator and support of third party app that was just "no, it is not our fault, something is not right on your system" (like every Windows Server just randomly decided to sometimes to delete files, right...)
So I decided to just collect evidences. Here is how to do it in Windows domain, but if you have stand alone server you can enable it as well with Local Policy.
First we need to create Group Policy with this settings:
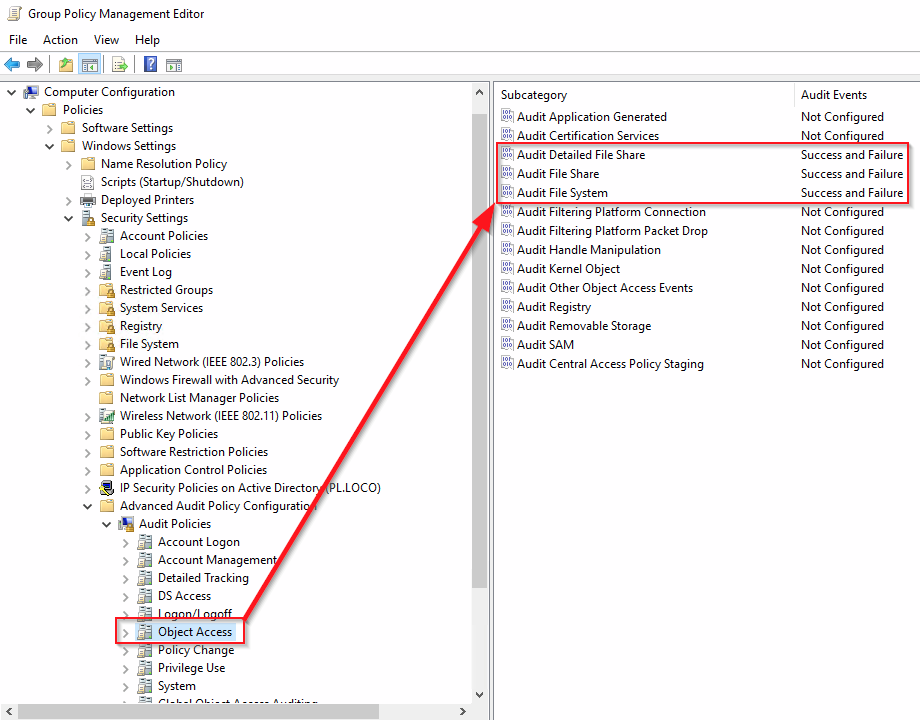
and link it to OU with server or on top of domain if you need it everywhere
Then we need to run gpupdate /force as Administrator to populate new GPO to servers/hosts
On server that need to be inspected we now need to enable auditing on directory that we want to investigate.
Choose Properties on directory, then Security, then Advanced button, and finally Auditing Tab. You should end up here:
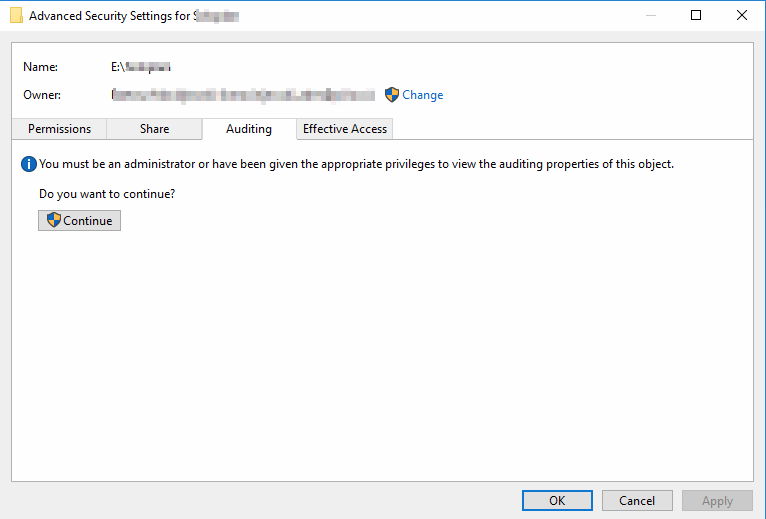
Click Continue to rise your privileges. Then click Add and add group Everyone or any set of users you want to track actions. Everyone is best to have whole scope.
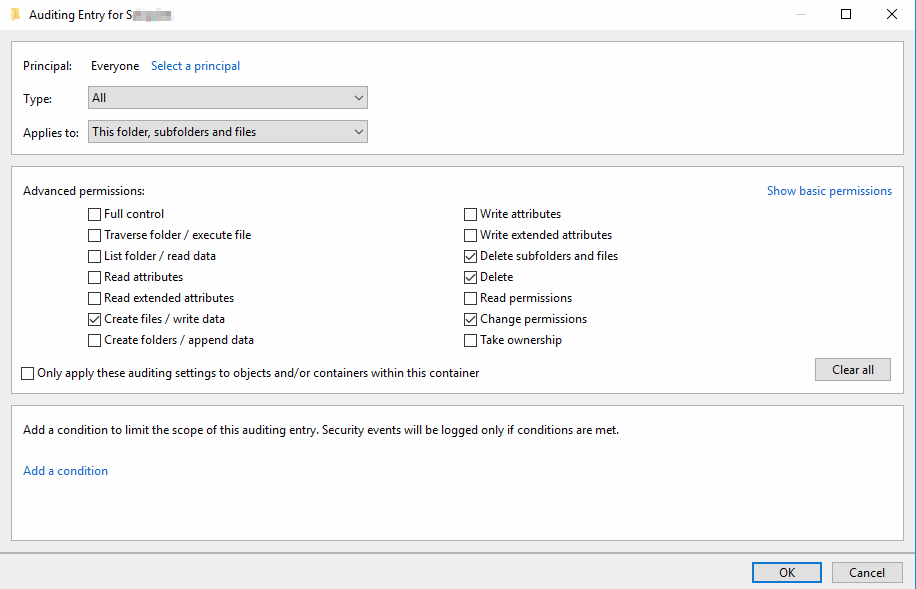
Click then Show Advanced Permisions, and choose what you want to monitor, especially mark Delete and Delete subfolders and files as those are not checked by default. Finally click OK.
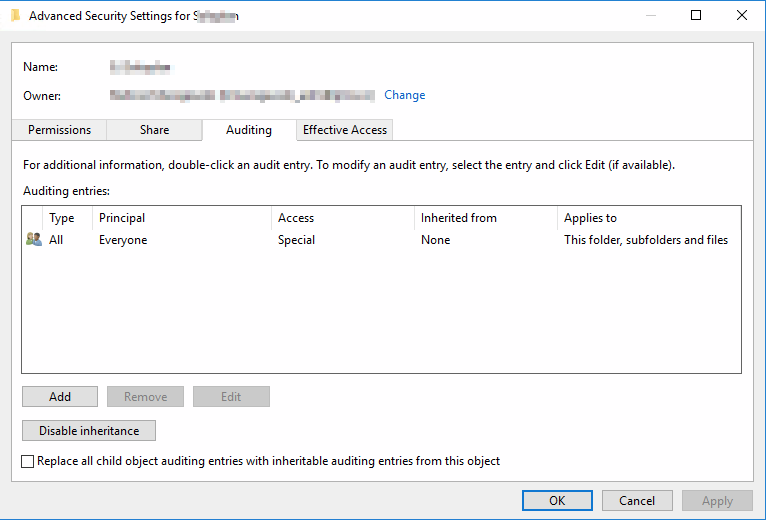
Configured auditing should look like this. After clicking OK, all ACL will be set on every folders and files and we are all set up.
Now for the results. You need to look Event ID 4660 in EventViewer in Security Log. There will be action taken of file/directory and who is responsible, but not yet exact file.
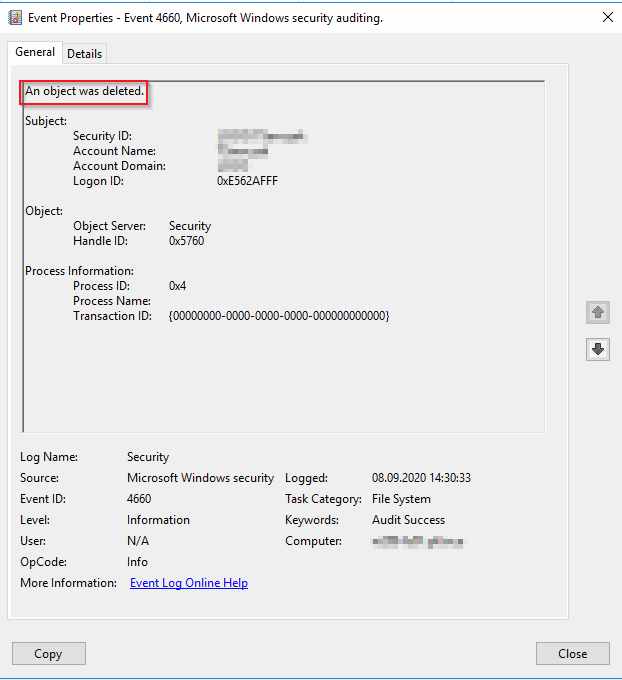
For the file or directory you have to look of Event ID number 4663. It should be just next to event 4660 or in the same second that 4660 occured.
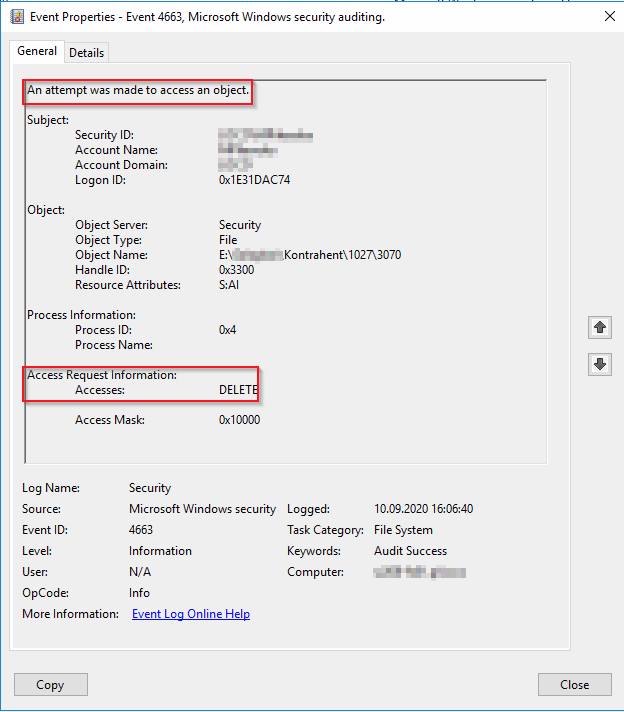
And finally take a look at Process information. When user is deleting file Process name is pointing to explorer.exe. When third party app is doing it there will be no explorer.exe.




